home
د. محمد بن ماطر حميد السلمي
وكيل معهد الدراسات والخدمات الاستشارية لتطوير الأعمال
قسم علوم الحاسب
أستاذ علوم الحاسب المساعد
قسم علوم الحاسب
كلية علوم الحاسب ونظم المعلومات
الاهتمامات البحثية:
-
التقنيات الذكية لإنترنت الأشياء بتطبيقاته المختلفة في أمن البحار والمحيطات وحماية الحياة والثروة البحرية وكذلك إمدادات صناعة النفط والغاز في البحار. (Internet of Underwater Things)
-
الحوسبة السحابية (Scheduling Schemes, Resource Allocation, and Load Balancing)
-
المدن الذكية (Smart Cities)
المؤهلات العلمية

الخبرات
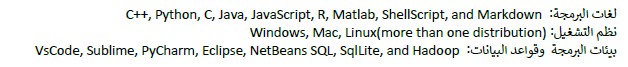
التخصصات والمهارات
الدورات التدربية
• Effective Algorithms for the Closest Pair and Related Problems.
• Flexible Hardware as the Key to Accelerating Optimized Neural Network.
• Security and Privacy in Intelligent Internet of Things.
• Memory Access Efficiency in Distributed Atomic Object Implementations.
• Data-Driven Techniques Against Cybercrime Operations.
• Novel Algorithms for Big Data Analytics.
• Composite Resource Management in Networked Control Systems.
• A framework for analyzing omics data using routes of biological pathways.
• Emotionally and Socially Aware Approaches to Understanding and Changing Users’ Cybersecurity
Behavior.
• Probabilistic Commonsense Knowledge in Language.
• The Effect of Experienced Emotions on User’s Trust in Automation.
• A Novel Tree Structure for Pattern Matching in Biological Sequences.
• Camera-based Attacks on Android Mobile Devices.
• Access Control across Isolated Containerized Environments in Linux.
• Building Fully Certified OS Kernels.
• Towards Provable and Scalable Machine Learning.
• Deep Pathway Analysis.
• Tolerant Algebraic Side-Channel Attack on Modern Ciphers using Constraint Programming.
• Adaptive Bitrate Streaming Over Cellular Networks: Rate Adaptation and Data Savings Strategies.
• Energy-Efficient Cache Architecture Towards Extreme-Scale Computing Systems.
• Efficient Sequential and Parallel Algorithms for Incremental Record Linkage.
• Securing Deployed Cryptographic Systems.
• An Algorithmic Framework For Gait Analysis and Gait-Based Biometric Authentication.
• Formal Modeling and Mining of Big Data.
• De novo repeats construction: methods and applications.
• The ALAMO Approach to Machine Learning: Best Subset Selection, Adaptive Sampling, and Constrained
Regression.
• Towards Secure and Trustworthy Cyberspace: From Network-centric to Information-centric Cyberdefense.
• Secure Computation: Minimizing the Trusted Computing Base.
• Securing Internet Routing.
• Deep Learning Systems for Automated Lesion Detection, Segmentation, and Classification in Mammography.
• Strengthening and Enriching Machine Learning for Cybersecurity.
• Towards Low-cost and Scalable Network Services: From Algorithms to Systems.
• Jointly Learning Features and Temporal Contingency for Prediction in Large Scale Datasets.
• Towards Privacy-aware Mobile Crowdsensing.
• A Configurable Framework for RBAC, MAC, and DAC for Mobile Applications.
• Probabilistic Controlled Airspace Infringement Tool and Conflict Resolution.
• Exploring Targets of Transcription Factors in Cancer Signaling Pathways.
• Geometry of Entanglement in the Bloch Sphere.
• Information-Centric Design and Implementation for Underwater Acoustic Networks.
• Performance Modeling for Cloud Platforms: A Data Driven Approach.
• Novel Algorithms for Some Fundamental Big Data Problems.
• Performance Prediction and Tuning for Large-Scale Data Analytics Systems.
• Computational Methods for the Analysis of Single Cell RNA-Seq Data.
• Hierarchical Bayesian nonparametric models and scalable inference in genomics.
• A Framework for Secure and Interoperable Cloud Computing with RBAC, MAC, and DAC.
• Efficient Algorithms for Trees and Networks in Evolutionary Genomics.
• Methods and algorithms for inference problems in population genetics.
• Exploring Targets of Transcription Factors in Cancer Signaling Pathways.
• Practicality and Application of the Algebraic Side-Channel Attack.
• Novel Algorithms and Applications for Data Mining and Machine Learning.
• Hierarchical Structures for High Dimensional Data Analysis.
• DeepCorr: Strong Flow Correlation Attacks on Tor Using Deep Learning.
• On the security of cloud storage systems and software supply chains.
• Privacy in the field: Protecting Sensitive Data for AI Applications.
• Inferring Microbial Gene Family Evolution Using Duplication-Transfer-Loss Reconciliation.
• Towards Detecting Routing-based Internal Attacks in 6TiSCH Architecture.
• Efficient Algorithms for Motif Search and Related Problems.
• Towards Security Analysis of OpenStack.
• A method to score pathways using heuristic rules.
• Algorithms for Circular Organelle Assembly.
• Lossless Compression Tools for Genomics Data.
• Cybersecurity Games: Mathematical Approaches for Cyber Attack and Defense Modeling.
• Constraint-based Sequential Pattern Mining with Decision Diagrams.
• Complex Genome Analysis with High-throughput Sequencing Data: Methods and Applications.
• Learning with Distributed Systems: Adversary-Resilience and Neural Networks.
• Deep Contextual Modeling for Natural Language Understanding, Generation, and Grounding.
• Human-in-the-Loop Entity Mention Mining from Noisy Web Data.
• Learning with Multivariate Time Series Data: from Representation to Applications.
• Information Extraction and Fusion for Improving Personal and Public Health Safety.
• Automated Reasoning of Security and Privacy of Cellular Networks.
• Building Secure Distributed Services and Resource Markets.
• NAIS: neural architecture and implementation search.
• Towards an Efficient, Scalable, Dynamic and Flexible NFV-based Data Plane.
• Machine learning for images in space and time: towards real-word applications.
• Computational Approaches for Inferring Units of Transfer and Modes of Integration for Horizontal Gene
Events.
• Developing Novel Copy Number Variation Detection Method using Emerging Sequencing Data.
• Security of Proof-of-Stake Blockchains.
• The Speedup Techniques for Deep Neural Networks and its Applications.
• Data-Driven Societal Cyber-Physical Systems.
• Bio-Specific Hardware Accelerators: From Emerging Devices to Bio- informatics Applications.
• Securing Operating System Kernels with Fewer Shots.
• Provably Scalable and Sample-Efficient Reinforcement Learning Using Policy Optimization.
الأبحاث العلمية
1. Alsulami, Mohammad, and Asadullah Shaikh. ”The Information-Seeking Problem in Human-Technology
Interaction.” International Journal Of Advanced Computer Science And Applications 7.5 (2016): 584-590.
2. M. Alsulami, R. Elfouly and R. Ammar, ”A Reliable Underwater Computing System,” 2021 4th IEEE
International Conference on Industrial Cyber-Physical Systems (ICPS), 2021, pp. 467-472, doi:10.1109/
ICPS49255.2021.9468139.
3. M. Alsulami, R. Elfouly, R. Ammar and H. Aldosari, ”Deployment of Multiple Computing Systems in
Underwater Wireless Sensor Networks,” 2020 IEEE International Symposium on Signal Processing and
Information Technology (ISSPIT), 2020, pp. 1-6, doi: 10.1109/ISSPIT51521.2020.
9408925.
4. M. Alsulami, R. Elfouly, R. Ammar and A. Alenizi, ”A Modified K-Medoids Algorithm for Deploying a
Required Number of Computing Systems in a Three Dimensional Space in Underwater Wireless Sensor
Networks,” 2020 IEEE International Symposium on Signal Processing and Information Technology
(ISSPIT), 2020, pp. 1-5, doi: 10.1109/ISSPIT51521.2020.9408730.
5. A. Alenizi, R. Ammar, R. Elfouly and M. Alsulami, ”Cost Minimization Algorithm for Provisioning Cloud
Resources,” 2020 IEEE International Symposium on Signal Processing and Information Technology
(ISSPIT), 2020, pp. 1-6, doi: 10.1109/ISSPIT51521.2020.9408841.
6. A. Alenizi, R. Ammar, R. Elfouly and M. Alsulami, ”Queue Analysis for Probabilistic Cloud Workflows,”
2020 IEEE International Symposium on Signal Processing and Information Technology (ISSPIT), 2020,
pp. 1-6, doi: 10.1109/ISSPIT51521.2020.9408967.
7. H. Aldosari, R. Elfouly, R. Ammar and M. Alsulami, ”Performance of New Monitoring Architectures
for Underwater Oil/Gas Pipeline using Hyper-Sensors,” 2020 IEEE Symposium on Computers and
Communications (ISCC), 2020, pp. 1-6, doi: 10.1109/ISCC50000.2020.9219687.
8. M. Alsulami, R. Elfouly, R. Ammar, H. Aldosari and A. Alenizi, ”Ideal Number of Computers for Real-
Time Underwater Computing Systems,” 2019 IEEE International Symposium on Signal Processing and
Information Technology (ISSPIT), 2019, pp. 1-5, doi: 10.1109/ISSPIT47144.2019.9001761.
9. H, Aldosari., Elfouly, R.S., Ammar, R. and Alsulami, M., 2020, March. New Monitoring Architectures for
underwater oil/Gas Pipeline using Hyper sensors. In CATA (pp. 307-316).
10. Alsulami, M., Elfouly, R. and Ammar, R., 2022. Underwater Wireless Sensor Networks: A Review.
المقررات التدرسية
Programming 1
Fundamentals of Programming
Software Engineering
Software Performance
Internet Technologies
Multimedia Technologies
Data Structures
Object Oriented Programming
Theory of Computation
Computer Applications in Health Science
Introduction to Computing for Engineers
Graduation Project1
Graduation Project2
الساعات المكتبية
الوصف
| 8-9 | 9-10 | 10-11 | 11-12 | 12-1 | 1-2 | |
|---|---|---|---|---|---|---|
| الأحد
Sunday | ||||||
| الاثنين
Monday | ||||||
| الثلاثاء
Tuesday | ||||||
| الأربعاء
Wednesday | ||||||
|
الخميس
Thursday |
